|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Weblog : News from the Lab
Tuesday, January 23, 2007
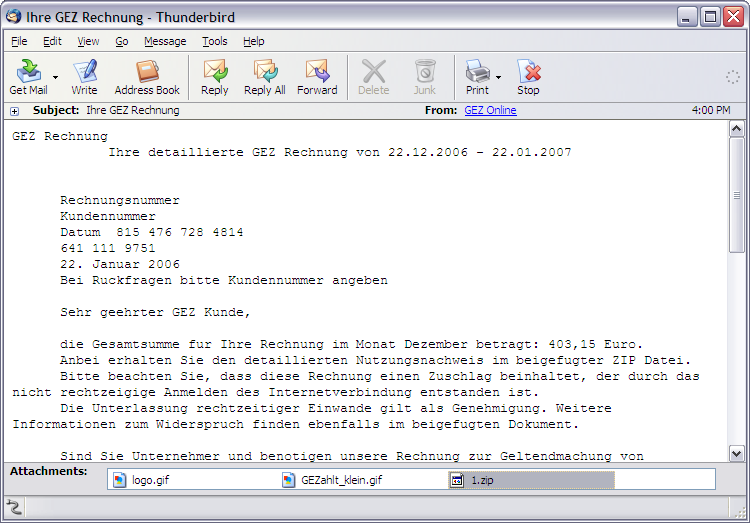
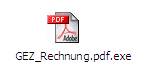
We have received many of reports from German customers receiving a spammed e-mail containing an attachment named GEZ_Rechnung.pdf.exe. Here is a sample screenshot of the spammed e-mail:
Our detection for this malware is Nurech.W. Nurech.W uses the following links to download Bzub.HO: http://buckells.co.uk/heidi/[BLOCKED]ex.txt http://samuraiwordsets.co.uk/images/[BLOCKED]p.exe Monday, January 22, 2007
This evening a new wave of the Stormy worm has been widely spammed. The subjects used in the e-mails have now changed from news-related events to love-related topics as you can see from the screenshot and the list of subjects below.
A list of subjects we've seen so far include:
Thanks to Diego who notified us and told us that this list looks very similar to the list of Romantic Cards over at 2000greetings.com and indeed it does. The list of files is much shorter: We now detect this as Email-Worm.Win32.Zhelatin.a. Note: For those of you who aren't already filtering EXE's in the e-mail gateway – do it now!
Our new laptop stickers have arrived! We started the contest several weeks ago. We then went through the results and selected the winners. And then we ordered up a batch and waited. Now we have them and stickers are everywhere in the lab.
The weblog readers whose suggestions were selected are: I lost my password, can you tell me yours? — Azham R. of Malaysia Their stickers were mailed out in the post today. Our thanks to all that contributed. Now that we have them, we'll use them as rewards for future challenges.
We analyzed a new Commwarrior variant last week. It runs on Symbian devices using Series 60 user interface – first and second editions. This variant of Commwarrior, enumerated as T, was otherwise quite uninteresting apart from the fact that it is newly compiled from the original source – unlike most variants. The author refers to it as "Commwarrior v3 Lite" in his code. In the mean time, we already have the detection published and we've updated our free F-Commwarrior utility that you can download from f-secure.mobi if you suspect your phone has been infected. This variant affects only Symbian Series 60 phones that use Symbian OS version 8.1 or older. This means that the latest model of phones that could be affected is the Nokia N72. Phones using Symbian OS 9.0 or later, such as the Nokia E70 or 3250, will not be affected.
Sunday, January 21, 2007
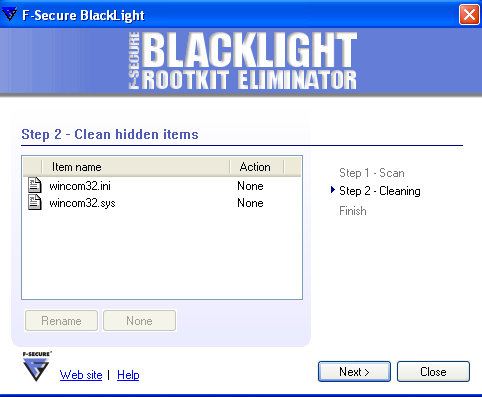
The weekend has been very busy with Storm Worm. We have lately discovered new variants that have started to use kernel-mode rootkit techniques to hide their files, registry keys, and active network connections. F-Secure BlackLight is able to detect the hidden files.
These variants are now detected as W32/Stormy.AB and Trojan-Downloader.Win32.Agent.bet. Saturday, January 20, 2007
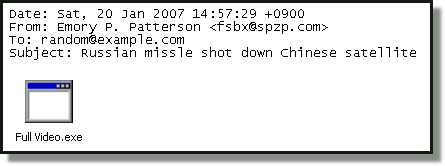
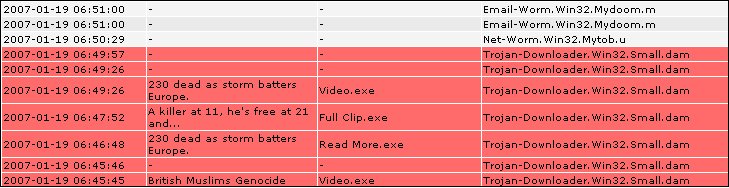
We got a repeat of what happened last night – but with a modified version of the trojan and fresh news items in the subject field.
This time the subjects in the mails are: And the attachment names are: When run, this malware creates a peer-to-peer botnet via port 7871/UDP or 4000/UDP. We detect this as Trojan-Downloader.Win32.Agent.bet. Update on Saturday: A few hours later, there was another run with new and modified variants. Mostly the same Subject fields, with the addition of: Update on Sunday: Another run. This time with a different theme included in the subjects: New filenames include Flash Postcard.exe. Detection for these is in our update 2007-01-21_04. Friday, January 19, 2007
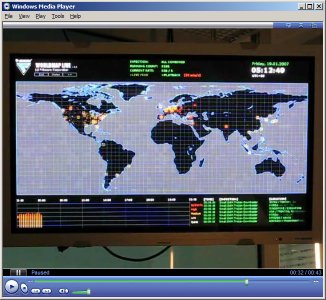
The Small.DAM (Storm-Worm) we posted on earlier spread very fast during the night, Helsinki time. The heavy seeding through spam was quickly obvious on our tracking screens. The worm was spread throughout the world very rapidly. Here is some footage of the worm's spread to share with our readers: The video is encoded with XViD (4651k). Also available via YouTube.
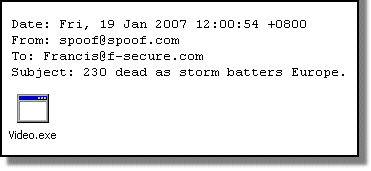
This morning we have been witnessing activities of Small.DAM being spammed.
Here are the possible subjects headings: The detection for Small.DAM was already included in our database update 2007-01-15_01.
Thursday, January 18, 2007
Oh man, there's a lot of spam out there nowadays. No wonder, too. The Warezov gang is using variants of Warezov and Medbot/Horst to send out medication and replica spam. The Rustock gang is using Mailbot.AZ and variants to send out stock spam. The Warezov gang is apparently operating from China and the Rustock boys from Russia. For more background info, read the "Connecting the Warezov domain dots" entry posted two months ago. Machines infected with Medbot use a client-server architecture. They connect to a central server to get further instructions as well as spam content and address lists. Then they get to the work of actually sending the spam. The server addresses keep changing. Last week seek21.zootseek.com was used to serve e-mail addresses to the bots. While investigating the case last week, we downloaded some 68 Gigabytes of e-mail addresses from this server.
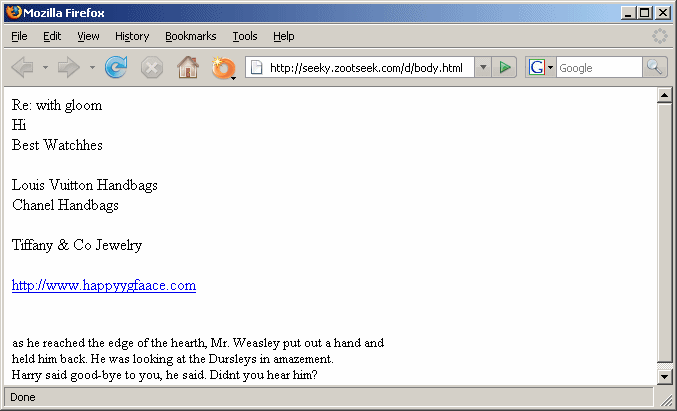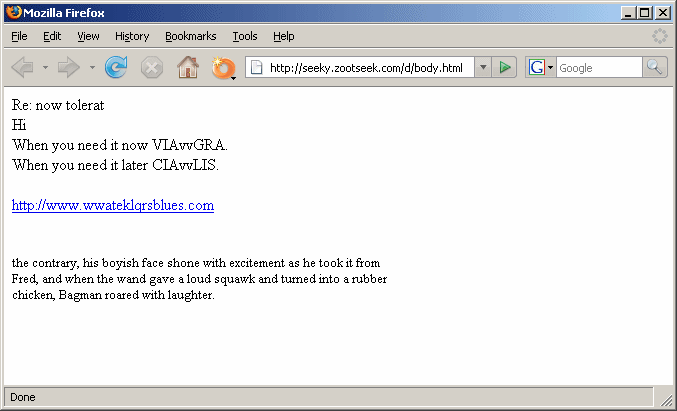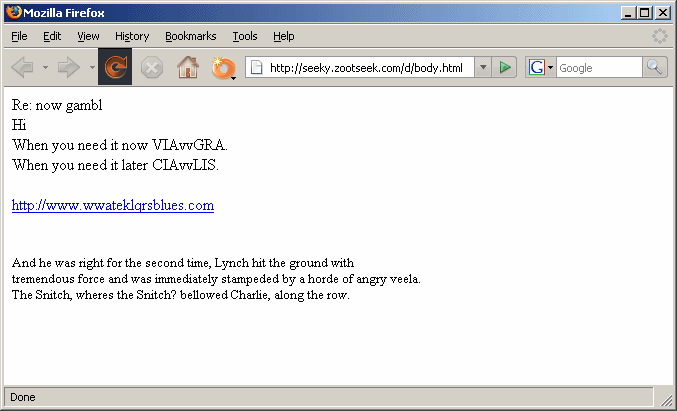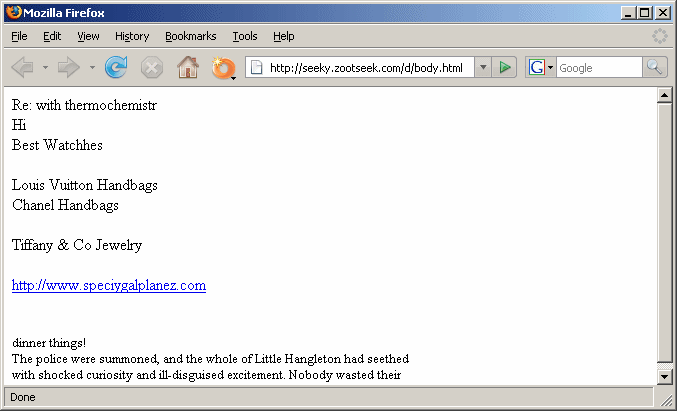
Another good example of the client-server architecture is the service running at http://seeky.zootseek.com/d/body.html. This URL serves randomized HTML templates for different spam mails. The URL is live at the moment of this posting. If you access it and reload the page, you'll get a different spam template every time (but do visit it at your own risk).
And by the way, you might want to block access to all hosts under the domain medbod.com (as it is used by Medbot to download updated bot code).
Fake web sites have been used to recruit money mules for quite a while. When cops investigate phishing or carding cases, the trail usually ends with the mule who might not have realized at all that he's actually laundering money for crime gangs. Here's one site mule recruitment site which is offline by now:
This morning I got a personalized mule recruitment spam. Emphasis below is mine:
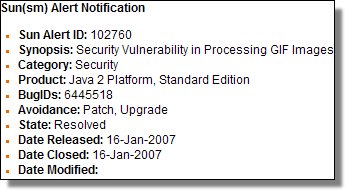
Last Thursday, we suggested that you update some of your applications… Well, on Tuesday, January 16th, Sun released an advisory regarding a vulnerability in processing GIF images in some versions of the Java Runtime Environment. When running a Java applet from a web page using a vulnerable version of Java Runtime, an applet exploiting the vulnerability may escape Java's sandbox. This means that the Java applet would have exactly the same access to the file system and process execution as any native application. Java vulnerabilities have been actively used by malicious web pages in the past, so it is quite possible that this new vulnerability will also be used. So do make sure that your Java runtime is up to date, instructions are available at Sun Advisory #102760. Note: Sun provides links to J2SE 5.0 Update 10 in their advisory. As we posted earlier, version 6.0 is also available from: java.sun.com. According to Sun, this vulnerability does not affect the Java versions used on mobile phones (J2ME). Tuesday, January 16, 2007
There's an update for the Acer ActiveX component vulnerability we posted on last week. Details can be found via US-CERT. The patch is named "Acer Preload Security Patch for Windows XP" and can be found here.
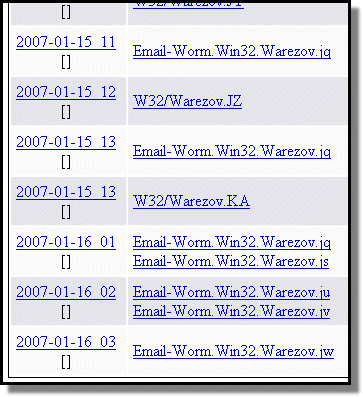
After a relatively short period of inactivity, Warezov has returned with about a dozen new variants in the last 24 hours. Variant KA received its moniker at the end of yesterday with update 2007-01-15_13. There is also a new domain to block: ertikadeswiokinganfujas.com. You'll find a more comprehensive list here.
F-Secure Internet Security 2007's System Control feature still automatically denies these latest variants. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [ Older News >> ] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
[Buy F-Secure Products] [F-Secure Frontpage] [Privacy Policy] [Legal Notices] [Contact Us]
Copyright © 2006 F-Secure Corporation
![Weblog [at] Our Domain](http://www.f-secure.com/weblog/archives/Weblog@.gif)